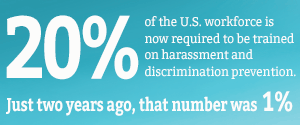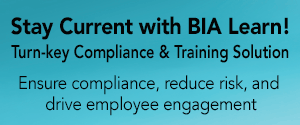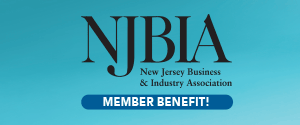
When the CrowdStrike IT outage struck back in mid-July, repercussions were felt across the globe. Hospitals, airlines, emergency service response systems and countless businesses were some of those impacted when the supposed routine software update failed and caused widespread disruption with nearly 8.5 million systems crashing simultaneously.
With many industries effected and the estimated billions of dollars in financial damage, the outage reinforced the need for strong cybersecurity protection. While this event was certainly unfortunate and unforeseen, so too are the many attacks that pose a threat to companies day in and day out.
Protecting yourself from the various risks that linger requires a proactive approach that requires constant management and testing of one’s cybersecurity system. Often that means preparing for not only the threats you know exist, but also the ones that you have not encountered before as bad actors evolve their technological capabilities.
Demetrios Roubos serves as Stockton University’s information security officer as well as an adjunct professor in computer science. From his viewpoint, the CrowdStrike outage undoubtedly raised some eyebrows, especially since the company’s tool works by gaining access to a computer at a very low level.
“It certainly caused alarm in the industry that this thing could happen in general and it alerted cybersecurity practitioners about the dangers of running such low-level tools,” he says. “Essentially, when one of those components at such a low level fails, like what we saw with the update that was pushed out there, it can create a catastrophic failure across all these systems. … Because their tool interacts at such a low level, it was able to create a service interruption that was very difficult for IT teams to mitigate.
“If was running a Fortune 500 company, one of my IT controls might take into account what driver-level services are being installed on my systems. As we saw with the CrowdStrike outage, a failure of that nature could grind the organization to a halt,” Roubos adds.
South Jersey Biz also spoke with several other tech experts from across the area to get a better sense of how companies can try and thwart future issues while boosting their overall cyber protection.
From your viewpoint, how did the recent CrowdStrike outage underscore the importance to be proactive with when it comes to cybersecurity?
“The recent CrowdStrike incident highlighted the potential risks associated with software updates. For instance, a software vendor may release updates for various reasons, including bug fixes, enhanced usability, new features and security improvements. However, without rigorous testing and proactive management, these updates can inadvertently introduce new issues.
“While these updates are essential to prevent vulnerabilities and enhance functionality, it’s crucial that both software companies and the managed service providers (MSPs) who utilize their software conduct thorough testing on dedicated test machines before deployment. This ensures that any potential issues are identified and resolved in a controlled environment, minimizing the risk of disruptions in live systems.
—Michael Barson, chief technical officer and co-founder, VoIP Doctors
“The CrowdStrike failure was due to a breakdown in testing before releasing for deployment. We believe everything should be rolled out in stages. Starting from testing in the lab, to testing a small subset of production computers prior to releasing to all systems. This way you make sure everything is working properly and tested before deploying. This methodology would’ve avoided the CrowdStrike failure.”
—James Gloner, vice president, Winstec Technologies
What kind of vulnerabilities exist when one vendor has the power to bring global industries to a screeching halt as we saw with this outage?
“CrowdStrike exposed the risk of vendor-induced vulnerabilities associated with choosing a single-vendor, without preparing redundant or alternative solutions. Having a single-point of failure can create a wide-spread bottleneck on supply chains, where even the smallest failure can shut-down all connected systems, as demonstrated by reliance on CrowdStrike in recent events. … To mitigate risks, companies can enhance security and adopt a zero-trust approach ensuring that every access request is verified, regardless of its origin.
—David Suleski, founder and president, #TechStarters
“CrowdStrike’s security platforms have certainly been immensely beneficial for organizations defending against cyber-attacks. Their success has resulted in greater adoption of their ecosystems and a ‘platformization’ approach to security. However, there is a legitimate question on the dangerous concentration of risk and denial of service vulnerability. This situation underscores the need for thoughtful diversification in critical services and technologies. Business resiliency should be a key component of any cost-benefit analysis when adopting these new technologies.”
—Divyesh Malkan, president, Information Systems Security Association-Delaware Valley chapter
Is there anything companies can do to be better protected?
“The recent CrowdStrike debacle highlights the critical need for proactive cybersecurity management. This incident underscores the importance of rigorous testing and validation of updates before deployment. It also emphasizes the need for continuous monitoring and incident response planning to quickly address and mitigate any issues that arise.
“To mitigate risks, companies can enhance security and adopt a zero-trust approach ensuring that every access request is verified, regardless of its origin. … To prevent similar failures in the future, companies can adopt staggered rollouts, invest in robust disaster recovery systems, regularly, and proactively review and improve cybersecurity policy and posture.”
—David Suleski
“All companies need to realize that a lot of what is being utilized is not new. Not meaning to burst anyone’s bubble here, but the cloud is not magic. Web sites that take the place of software you used to purchase and install on your server is not a cheap silver bullet, and nothing in the cloud is actually cheaper. To that end, companies need treat any cloud or web-based solutions just like they did when they had a data center. It needs to be backed up. You need a redundant system, or secondary system, or downtime manual process for everything you deem critical. The reason some outages are so severe is because of the lack of investment in disaster planning and redundancy. So often, this is left out of return on investment calculations when deciding to move to the cloud in the first place, and as such, businesses are investing in solutions that are not on par with their previous systems.”
—Darren Crane, president, DLC Technology
How hard does a company have to work to regain consumer trust after such a huge misstep?
From a reputational perspective, CrowdStrike certainly has suffered an impact and time will tell in how that effects customer retention. How an organization responds to customer needs in the immediate aftermath of an incident is crucial to re-establishing trust. Doing so requires transparency, accountability and consistent communication. Companies must not only acknowledge the misstep but also demonstrate a commitment to rectifying it.
—Divyesh Malkan
How is the advancement of AI making an impact in VoIP technology and will it change the way customers approach security at all?
“AI is often seen as a beacon of innovation and progress, but from a security perspective, it’s not all positive. The FCC and multiple state governments are scrutinizing AI, with some already banning its use in certain industries and applications.
“Several months ago, a large financial institution faced significant fines for using AI to analyze customer calls without proper consent. More recently, I’ve encountered AI-driven robocalls that mimic human interaction so convincingly that they followed up with phishing emails, urging me to click on malicious links.
“While AI’s capabilities are impressive, we must remain vigilant about its potential risks. It’s crucial to appreciate what AI can achieve, but also to be cautious about the security threats it can pose.”
—Michael Barson
Every business owner has different needs, but what is your most basic advice to companies considering making a change to bolster their cybersecurity?
“To defend against an increased rate and range of attacks. Businesses need to take a multi-layered defensive approach that overlaps safeguards, limited access points, user training and perimeter defenses. Essentially modern companies need to become digital fortresses with multiple layers of proactive protection that serve to monitor, detect, alert and prevent the onslaught of cyber-attacks. I would recommend the following approach:
- Identify protection and access management
- Endpoint security
- Email security
- Data protection
- Web+ network security
- End user training
- Mobile security
- Disaster recovery with a backup and incident response plan.”
—James Gloner
“It is impossible to protect your business with a single piece of software. Develop a cybersecurity program and stack of protections that provides the protection you need in accordance with the frameworks required by your industry. After that is in place, buy cyber insurance—this will save you money. If you don’t have the expertise in house, there are many cybersecurity focused service providers that can help. In today’s climate, quite literally no business is too small for this advice. Even a one-person company needs to fight the same advisories as a Fortune 500 business.”
—Darren Crane
Click here to subscribe to the free digital editions of South Jersey Biz.
To read the digital edition of South Jersey Biz, click here.
Published (and copyrighted) in South Jersey Biz, Volume 14, Issue 10 (October 2024).
For more info on South Jersey Biz, click here.
To subscribe to South Jersey Biz, click here.
To advertise in South Jersey Biz, click here.