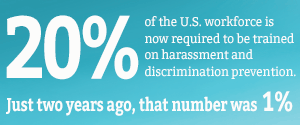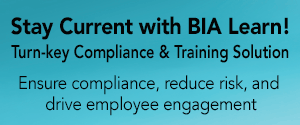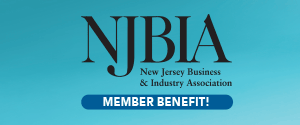
Financial services. Health care. Construction. Food and beverage. As with the rest of the world, when it comes to business industries, there isn’t one that hasn’t been affected by the pandemic. While most were negatively impacted, there are many that have been able to thrive. For as much of a hit that restaurants and their suppliers have faced, the warehousing industry is booming, for example. No matter how the past year has gone, there is one thing for certain—it’s unlikely business will ever be done the same way again.
“If the pandemic has taught us anything, it’s the need for the mobile office,” says Andrew Kazelis, vice president of operations for USA Phone. “Being able to take your office and business telecommunication system on the road is no longer a luxury—it’s become a necessity.”
While the saying goes that ‘change is good,’ no one saw the changes of 2020 coming. So, the systems that were quickly—and perhaps haphazardly—put into place, will need to be evaluated and refined for best practices in the months to come.
Undoubtedly, if 2020 was the year of change, 2021—and beyond—will be the year of continued adaptation. Finding solutions that adjust to the new ways of doing things while still managing to grow and expand will be key.
Fortunately, experts suggest these solutions may be found in the platforms that are already being utilized.
“Teams. Zoom. Slack. Those three are the major programs, but there are many others,” says Art Leiby, president of Lerepco IT Group. “The whole concept of being able to communicate and collaborate—whether you’re sitting in the office, at home or in a hotel—and you’re able to have a video conversation or an audio one, that has really changed and been accepted in 2020.
“Where maybe people were resistant in the past to do this type of thing … Now, everyone is there,” he continues. “They were resistant to putting email up in the cloud. They didn’t trust Microsoft 365. If it wasn’t behind locked doors, they didn’t want it. But now they do.”
As a result, many businesses are likely to opt to downsize their brick-and-mortar footprints. Not only are the number of offices not required anymore, but with the increased comfort level of the cloud and mobile accessibility, entire data centers are being downsized as well.
While many may have already been forced to consider these changes over the last year, more will continue to do so, Leiby says, with the realization that business can be done from home.
“Microsoft, for example, is going to work harder and harder to make cloud voice what everyone uses,” he suggests. “They’ve also come up with a new solution similar to Teams. Everything is going to be done over the internet.”
Though productivity may be a concern from home, Ravi Shankar, CEO of Fourth Technologies, suggests there are now systems to help monitor employees to keep them on track.
“There are a lot of things which would help the business owner still have a realistic picture of what’s going on,” he says. “It can be done by phone and also by subscribing to a sales monitoring system.
“You can keep track of calls on an Excel spread sheet, but you won’t be reminded that way to give someone a call back,” he continues. “There are programs that will set reminders and let you know what calls you have made.”
Of course, the major concern that had kept everyone from going to the cloud in the first place is still a viable one—security. This is especially true now with employees working from home who are not safe under the security umbrella of the business’ server.
“The latest and most damaging threats facing businesses today are the use of email to launch ransomware attacks, install malware to an unsuspecting victim’s computer, steal a user’s login and password information or use email to impersonate a user to commit bank wire fraud,” says Timothy Guim, president and CEO of PCH Technologies. “All these threats prey on the user to take swift action in clicking a link or providing information without confirming the validity of the source. These threats can cost the business real money in the case of wire fraud, their business can be brought to a halt in the case of a ransomware attack, or in the worst case, an attacker can gain access to the system using malware to create a data breach and steal information.”
Though not every security breach is as significant as what happened with IT company SolarWind in 2020, when hackers accessed its system and were able to send malicious codes out to thousands of companies, even the smallest breach can have an affect on a small business.
“Businesses need to take cyber security threats seriously, regardless of their size,” Guim adds. “There needs to be a commitment from the executive level, understanding the importance of cyber security and use of a framework to craft a plan to protect the data and business continuity.
“Data need to be protected and rings of security needs to be placed around it,” he continues. “Backups with the ability to recover quickly are very important. Technology needs to be in place to have visibility into the systems in order to detect security threats as soon as possible. Also, all businesses should ensure they have the proper amount of cyber liability insurance based on their needs.”
Michael T. Geraghty, director for the New Jersey Cyber Security and Communications Integration Cell (NJCCIC) agrees, and suggests businesses address cyber security before there is a threat.
“They have to look holistically, instead of reacting ad hoc to every new threat,” he says. “Instead of saying, ‘Oh my goodness, there’s ransomware,’ they need to do a risk assessment and see how their system would respond to an attack.”
Geraghty says there are a number of great frameworks businesses can mirror that will allow cyber security to be addressed in an organized manner, including ones from the National Institute of Standards and Technology and the Center for Internet Security.
“They both have frameworks that allow the business to look at cyber security holistically,” he says. “Then a business can figure out what they’re doing well, and also look at the gaps and fill those in, instead of waiting for something bad to happen.”
Leiby says another safeguard is ensuring employees are using business-provided equipment to work from home.
“This is one of the biggest concerns,” he says. “It has the antivirus. It has the anti-malware. The difference is, when you’re sitting in an office, you’re behind a firewall which offers security and protection. The same employees working from their own homes don’t have that level of security.”
Also, educating employees on what they should and shouldn’t do—to click or not to click—when they receive an unusual email or request is key. This can be done through simulations that only take three to four minutes to complete, but offer the knowledge employees need to ensure they’re being as careful as possible, while encouraging them to call IT if they find themselves in a situation where they don’t know what to do.
“The biggest fear is ransomware,” Lieby says. “When they download something they shouldn’t or open an email they shouldn’t. We’re entrusting our users more than ever before to be productive working from home, but they are the single greatest weakness in the link.”
Multifactor authentication is also key, according to Geraghty. This is an extra factor, or step, in the log-in process, that can ensure the user that is requesting to access the business network is actually supposed to be accessing it.
“So many passwords are stolen and it’s easy to log in with that compromised password,” he says. “Multifactor authentication means an SMS (short message service) is sent to a cell phone or there is an authenticator application on your cell phone—an extra factor to confirm that it is you trying to log in.”
If there’s anything for certain, this pandemic has changed the way people work. Expectations have changed. Hours have changed. What used to be considered a luxury—working from home—is now the new normal. But it has opened businesses up to a whole new level of security uncertainty, and continuously working to keep themselves safeguarded will be essential in the months to come.
“A new approach needs to be taken to properly protect employees wherever they may be working,” says Guim. “It is important to have robust multi-layer security in place for all devices accessing corporate data.
“Part of these layers include using advanced AI (artificial intelligence) email protection, advanced AI endpoint protection, and security log monitoring backed by 24x7x365 SOC (security operations center), to keep eyes on any cyber threats occurring with remote work employees,” he concludes. “This level of security monitoring allows issues to be identified and resolved quickly versus letting the threat go undetected and turn into a much larger cyber incident.”
To read the digital edition of South Jersey Biz, click here.
Published (and copyrighted) in South Jersey Biz, Volume 11, Issue 3 (March 2021).
For more info on South Jersey Biz, click here.
To subscribe to South Jersey Biz, click here.
To advertise in South Jersey Biz, click here.