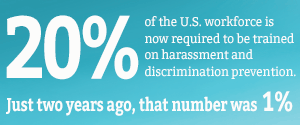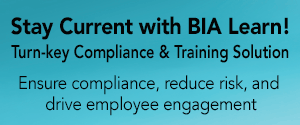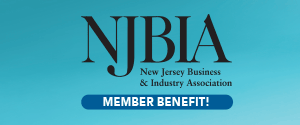
Computer viruses always bring trouble, but what about when it happens to your business computer? We asked Erwin Racimo (pictured), IT coordinator for the New Jersey Tech Council, to let us know what to do if your system is compromised.
1. Symptoms of Possible Hacking or Infection
• Your computer cannot open programs
• Your browser’s homepage has been changed and redirects to another site
• A popup window appears and tells you that you need to scan your computer now. After scanning, the program informs you that not all suspected infection has been removed and prompts you to upgrade the software in order to remove all infection. Another telltale sign is a warning window from your antivirus program that a virus has been detected and it becomes unresponsive.
• You cannot open files from your documents folder and it informs you that these files have been corrupted.
2. What to do when you suspect an infection
When your computer belongs to a network or a workgroup, unplug your ethernet cable or connection from your cable modem or wifi right away. Determine what type of infection by writing down what is displayed on the popup windows. If you have additional computers at home that are not infected, search for the particular infection and print out step-by-step instructions to remove it. Beware, there are many sites on the Internet that will provide you utilities or programs to remove infection whether paid or free but laden with advertisements that hide as malware or adware when you click on them which further aggravates your computer. Always use trusted sites such as Microsoft, CNET, Malwarebytes Antimalware, Kaperski and other reputable companies.
• Shut down your computer and restart in Safe Mode. In this mode, it only allows the computer to fix most, if not all problems relating to the operating system. In addition, safe mode is also used in removing rogue software.
• Check if there are new programs that were installed and remove them via add & remove programs.
• Install the utilities that you have downloaded from the USB drive.
• Scan your computer according to the instructions provided for that particular infection. The scanning process can take from three to six hours including required restarts and depends on the size of your files on your hard drive. Continue rescanning until all the infections have been eliminated.
• Restore your files and settings preferably from your backup file. External flash drives like Seagate and Western Digital come bundled with auto backup or sync software so that you can restore your files in case they get infected or corrupted.
3. Check your online accounts Many free personal email service providers like Google, Outlook, MSN, etc., employ outstanding heuristic scanning methods of inbound emails, and emails that are 99.9 percent spam are automatically directed to your junk folder and marked as such. Monitor your inbox for newsletters that you have subscribed to. Unsubscribe to newsletters that you no longer read. Newsletter emails that you did not opt-in to should be treated as junk or spam. Check if you can log in to your email account. If not, your account was also compromised. Check your bank accounts if you do online banking. Change your password monthly or as often as you like and create a complex password that include nine or greater alphanumeric characters.
4. Notify those on your contact list Alert them not to click on any links that may have been included on your emails. Tell them not to open suspicious emails including attachments. Delete them immediately.
5. Update your computer Install the latest version of updates from your computer’s manufacturer, including drivers and other third-party software that you may have. The best defense is a great offense—invest your money in a great antivirus software. Not all “free” antivirus software is created equal. Your antivirus software should be complemented with other third-party utilities to defend against malware and other threats.
Published (and copyrighted) in South Jersey Biz, Volume 5, Issue 2 (February, 2015).
For more info on South Jersey Biz, click here.
To subscribe to South Jersey Biz, click here.
To advertise in South Jersey Biz, click here.